

Table of Contents
Introduction
Electronic Frontiers Houston
Presents:
Pretty Good Privacy
(PGP)
Workshop
How to use Pretty Good Privacy
Paul Elliott
pelliott@BlackPatchPanel.com
PMB 181, 11900 Metric Blvd Ste J. Austin TX 78758-3117 (512)837-1096
It has become apparent that the data super highway is not safe. Messages
traveling the data highway can be hijacked by sinister data interlopers.
After six months of unpaid labor, in June, 1991 Philip Zimmermann released
his controversial freeware program Pretty Good Privacy (PGP). Just as Prometheus'
liver was eternally chewed by eagles for the crime of bringing fire to
mankind, Philip Zimmermann's liver was chewed by the Federal Eagle (The
U.S. Custom Service) for the alleged crime of releasing strong cryptography
to the world.
As a result of Philip Zimmermann's contribution, you can use the widely
available freeware program PGP to send electronic-mail messages to anyone
in the world, in complete privacy! In addition you can send authentication
with your messages so that the recipient can verify that the message really
came from you. You can encrypt sensitive files on your computer so that
the files remain private even if your computer and disks are stolen.
On January 14 1995, at 3:00 PM at the offices of South Coast Computing
in Houston, Texas, the Electronic Frontiers Houston and Paul Elliott presented
a Free Cryptography Workshop: How to use Pretty Good Privacy (PGP).
This workshop was designed to teach people how to use PGP effectively.
This document summarizes that workshop.
The original has become obsolete, so this modified version clarifies the use of GPG, PGP's free software successor.
The History and Philosophy of PGP and GPG
History before PGP
In the beginning, nobody needed encryption, because no one could write!
Then, after many years of struggle, writing was invented! But there was
still no problem, because only the rulers and their trusted servants could
read or write. But, as time went on, more and more people learned to read,
and there began to be a problem with written communications, in that if
someone hostile intercepted a written document, they could read it!
This began a war between the people trying to find ever more complicated,
neat ways of scrambling messages and the people trying to figure out ways
of descrambling them. Sometimes the people scrambling messages would win,
and sometimes the people descrambling messages would win. As time went
on, this war over ciphers became intertwined with regular wars, and things
got interesting! In spite of cryptography's use in wars, cryptography
was
invented by civilians.
And it was used by civilians through out its
history.
Anyhow, the first ciphers were single key or conventional
or symmetric ciphers.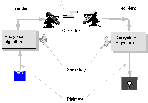 In
single key ciphers, there is one key that must be used by both the sender
to encrypt, and by the recipient to decrypt. The message can be decrypted
by anyone who possess this key. This leads to the key
distribution problem.
In
single key ciphers, there is one key that must be used by both the sender
to encrypt, and by the recipient to decrypt. The message can be decrypted
by anyone who possess this key. This leads to the key
distribution problem.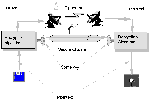 There
must be some way to insure that both the sender and the recipient have
the same key. Care must be taken so that unwanted parties do not posses
this key. It is necessary to have some kind of secure channel to accomplish
this. The problem with secure channels is that they are difficult to establish
and that people are always trying to compromise them.
There
must be some way to insure that both the sender and the recipient have
the same key. Care must be taken so that unwanted parties do not posses
this key. It is necessary to have some kind of secure channel to accomplish
this. The problem with secure channels is that they are difficult to establish
and that people are always trying to compromise them.
Then Rivest, Shamir, and Aldeman invented Public
Key Cryptography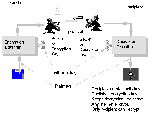 and
the algorithm that bears their name, RSA.
The
RSA algorithm is based on the mathematics of exponentiation.
and
the algorithm that bears their name, RSA.
The
RSA algorithm is based on the mathematics of exponentiation.
In this scheme, there are two keys, an encryption or public
key and a decryption or secret key. The Recipient creates
both keys. The encryption key is published. The decryption key is kept
secret. Thus, anyone can encrypt and send a message to the recipient, but
only the recipient can decrypt. This encryption scheme solves the key distribution
problem, since the only key that the sender needs can be published without
compromising the messages. It can be sent via any unsecured channel.
PGP is created
In 1991, Senate Bill 266 proposed that all private encryption
software would be required to be afflicted with a government backdoor.
This outraged Philip Zimmermann, who responded by writting PGP version
1.0. The original version was flawed. It featured a weak half baked
symmetric encryption algorithm that had to be replaced. This was replaced
with a workable algorithm called IDEA, resulting in a working public
key encryption program available free to the public.
Just as Prometheus'
liver was eternally chewed by eagles for the crime of bringing fire to
mankind, Philip Zimmermann's liver was chewed by the Federal Eagle (The
U.S. Custom Service) for the alleged crime of releasing strong cryptography
to the world.
PGP is replaced by GPG.
PGP was standardized, but as time went on PRZ showed an annoying
fascination with proprietary software schemes. This caused Werner
Koch of Germany to write GNU Privacy Guard, (GPG), a GPLed, free software implementation of the PGP standard.
GPG is the PGP standard compatible encryption program in a Linux environment. For Linux, GPG has effectively replaced PGP.
PGP GPG is a hybrid program
Now, from your point of view of as a user of PGP GPG, PGP GPG behaves as if it
were a Public Key Encryption program. A you create a secret/public key
pair and publishes the public key. But internally, PGP GPG
is a hybrid encryption program. When
PGP GPG encrypts a file, it creates a random conventional encryption
key. It sends that key to the recipient using a header block that is encrypted
using
RSA DSA public key encryption. Thus RSA DSA serves as the secure
channel which is used to transmit a conventional key, solving the key
distribution problem. The bulk of the message is encrypted using a conventional
cipher, IDEA AES. PGP GPG uses this scheme because
RSA DSA encryption
is very slow, so that if the whole message were encrypted with RSA DSA,
then PGP GPG would be too slow. IDEA AES is thought to be a stronger encryption
method than
RSA DSA so this scheme does not weaken PGP GPG.
When
PGP GPG encrypts a file, it creates a random conventional encryption
key. It sends that key to the recipient using a header block that is encrypted
using
RSA DSA public key encryption. Thus RSA DSA serves as the secure
channel which is used to transmit a conventional key, solving the key
distribution problem. The bulk of the message is encrypted using a conventional
cipher, IDEA AES. PGP GPG uses this scheme because
RSA DSA encryption
is very slow, so that if the whole message were encrypted with RSA DSA,
then PGP GPG would be too slow. IDEA AES is thought to be a stronger encryption
method than
RSA DSA so this scheme does not weaken PGP GPG.
Now, PGP GPG stores keys in keyrings. Usually, public keys are stored
in a file called
pubring.pgpgpg and secret keys are stored in a file
called
secring.pgpgpg.
PGP GPG uses conventional encryption to protect secret
keys
How does PGP GPG help you keep your secret keys secret? RSA DSA secret and public
keys must be hundreds of bits long and they are must be chosen randomly.
This presents a problem. If PGP GPG were to ask you, a human being, to remember
your public key, it would be inconvenient, because most human beings do
not remember long strings of binary information well. You might write it
down. This would be bad, because someone might do a black bag job
on you. A black bag job is when a practical cryptoanalyst comes
to your house when your are not there with a bunch of locksmithing tools
in his black bag. He comes away with your secret key in his black
bag. The other alternative would be to store your secret key in a computer
file. But this risks someone doing a black bag job on your computer.
PGP GPG solves this dilemma by storing both your public and secret keys in
computer files called keyrings. But, it stores your secret key encrypted
with conventional encryption. Your secret key will be protected with a
pass
phrase which you must specify every time you wish to use your secret
key. (When you decrypt a message or sign a message.) Hopefully, you will
choose your pass phrase so that it will be easy for you, as a human
being, to remember it.
PGP GPG scrunches your pass phrase to a 128
bit cryptographic checksum, using an algorithm called MD5 SHA1. (English
has a entropy of about 1 bit per character, so if you use a pass phrase
128 characters long, then all values for the checksum will be equally possible.)
This checksum is used as a conventional key to encrypt or decrypt your
secret key, using IDEA AES.
The upshot of all this is that your secret key is stored on a file on
your disk. Thus your disk must be carefully backed up. The secret key is
encrypted, so that you must specify a pass phrase anytime you wish to perform
an action that uses your secret key. Thus you will be asked for your pass
phrase when you wish decrypt a message, or when you wish to sign a message.
You should choose your pass phrase so that you can remember it, but no
one else can guess it.
PGP GPG Can Authenticate Messages.
PGP GPG can authenticate or sign messages. You can create digital signatures.
A digital signature is additional information that tends to show that a
given document really came from a given person. PGP GPG can check digital
signatures to check if a given document for tampering.
How
does PGP GPG authenticate a message?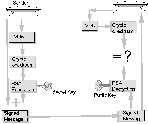
What do digital signatures prove?
A PGP GPG digital signature shows that the person who signed the document had
access to the PGP GPG secret key and the pass phrase for the
key indicated by the signature and that the document has not been modified
since it was signed. This is different than hand writing signature authentication,
which ultimately depends on the nervous system of the signer.
Publish your public keys?
Since PGP and GPG are public key programs, you must publish your public
keys. Without your public keys, no one can send encrypted messages to
you. No one can authenticate signed messages you send.
How to publish your public keys?
A lot of people have used a lot of non-standard, inefficient and
basically dorky methods of making public keys available. People have put
their pgp key on their web pages, put their keys in their mail
signature blocks, but nobody has put their public key blocks up on a
bill board!
The effective, standard, practical way to publish your pgp public keys is to put them on the PGP keyservers. This is the method that other pgp users and the programs they use expect you to use. This is the method you should use.
It is only necessary to send your public keys to one PGP keyserver. They are like small town gossips. They all talk to each other. To tell one is to tell them all.
What is the Job of a PGP keyeserver?
The job of a PGP keyserver is to remember the keys that people send
them and to make these keys available to everyone. The PGP keyservers
do not authenticate keys sent to them. Its not in the job description.
Just because a public key appears on a keyserver, does not mean that that key can be trusted. It could be a fraudulent key.
How are PGP keys authenticated?
PGP keys themselves can be signed. Instead of a centralized authority
that signs keys like some other encryption/authentication systems. PGP
uses the "Web of Trust". Anyone can sign a key and authenticate it.
The only questions is who's signature do you trust on a PGP signature.
Personally, I would more likely trust a friend, rather than some big
organization subject to governmental and institutional pressure. Those
old Romans had it right: "Quis custodet ipsos custodes?" that is "Who will guard these self-same guardians?" PGP/GPG allows the user to decide who he wishes to trust.
So how do I know this key is good?
How do we know that a given key actually belongs to the person indicated?
A fraudulent key can be created to trick us into accepting bad signatures.
It could be used to trick us into encrypting a message that the wrong person
can decrypt. It is possible to forge an email message, so we can not necessarily
trust that the email message that brought us a public key was not fraudulent.
As we have seen, the public keys servers do not check
that the keys stored in their databases are correct.
The first and most basic way of checking a public key is to contact
the owner directly. You could call the owner on the phone, and ask the
owner if the key you have really belongs to him. Then if you recognized
him by voice, you could be sure you had the right key. But how would you
know that you and the key owner were talking about the same key? He could
have a key with key identifier and you could
have a fraudulent key with the same key identifier. How would you check
this? The answer is the -kvc --fingerprint option:
pgp -kvc key-identifier
gpg --fingerprint caperry@ticom.com
This will cause pgp to print a fingerprint that looks like this:
pub 1024D/3FAF7DC2 2002-05-20
Key fingerprint = 920D 8C43 B3F4 EEE6 1626 0091 4636 E4E4 3FAF 7DC2
uid Carl Perry (TICOM Inc.) <caperry@ticom.com>
uid Carl Perry <cperry@ticom-geo.com>
sub 2048g/E07CEF04 2002-05-20
Kgpg and seahorse also display key fingerprints.
The key fingerprint of a given key is designed to be unique. If two people
get the same key fingerprint for a given key, then they know that they
are dealing with the same key. Key fingerprints can be used to verify the
validity of keys over the phone. We now pass on to more indirect methods
of checking the validity of keys. Some people put their key fingerprints on their business cards.
Key Signatures
Key signatures are used to transfer the knowledge of the "goodness" of
a given key from one person to another. Let us do a thought experiment.
Suppose that Judy has received a key from Fred through email, and she needs
to verify that it is really Fred's key. She does not know how to contact
Fred directly, but she has a friend, Sally, who does. She already has Sally's
valid key. She (Judy) could get Sally to send her a PGP GPG signed message
like this:
-----BEGIN PGP SIGNED MESSAGE-----
Hash: SHA1
I know of my own personal knowledge that the key
with key fingerprint:
F6 C7 33 D8 64 07 46 D7 FD 67 53 80 CE 7E 0B C8
Really does belong to Fred!
Sincerely, Sally
-----BEGIN PGP SIGNATURE-----
Version: GnuPG v2.0.4-svn0 (GNU/Linux)
iD8DBQFJidAwiv9zpDRc3ZkRApARAJ9rvLV6LDLzekE2comfFZQ6RmsZNwCgjhcF
kfRzaMl4gjXMOVW2PCjme8I=
=L4yQ
-----END PGP SIGNATURE-----
Judy can run this message through PGP GPG to verify that it really came
from Sally. She can check the fingerprint against the fingerprint she has.
If the fingerprints match, and she trusts Sally, then
she can be sure that the key really is Fred's key.
It is never necessary to actually send or create messages like the above.
PGP GPG supports the same functionally through the concept of "Key signatures".
When one signs a key, one is essentially creating a message like the above,
and attaching it to the key itself on the key ring! Then, when a key is
extracted
from a keyring, and sent to someone else, and added
to another keyring, the "key signature" goes with it! Thus key signatures
propagate from user to user in the same way that keys do. To sign a key:
pgp -ks the_key_id_you_are_signing -u the_key_doing_the_signing
You can sign keys and view signatures using kgpg or seahorse. Whenever you sign a key, you should re-send the key to the
public
key servers so that other PGP GPG users can use the signature to determine
the validity of the key. This can be done with kgpg or seahorse.
When should I sign a key?
You should sign when you know of your own personal knowledge, that the
key belongs to the person indicated. If you do not know the person,
check id. You should not sign a key on the basis of an inference. Let
other people make their own inferences. If you wish to trust a key for
your own personal use, on your own computer, you can "locally sign" or
"lsign" a key.
Overview of PGP GPG
PGP GPG is not an "user friendly" Program
PGP GPG has no menus. there are no mouse buttons to click. PGP GPG will not paint
a fancy picture for you to look at and it will not cause sound to come
out of your computer. PGP GPG is a unix style command line program. The direct
way to use PGP GPG is to enter a PGP GPG command. This command will typically include
computer filenames, key identifiers and options. Options begin with the
"-" character followed by a string of incomprehensible letters.
The good news is: "No one has to enter PGP GPG commands directly."
PGP and GPG are used almost exclusively for mail. Interactive encryption is typically done by ssh or ssl.
Almost all modern mail clients can create and handle PGP/GPG encrypted messages. If yours can't, get rid of it.
PGP/GPG key management can be done by point and clicky GUI programs like KGpg and/or seahorse.
There is a PGP GPG extension to
GNUEMACS
.
PGP GPG Web Pages
How PGP GPG handles text.
There are two separate problems that encryption programs have in dealing
with text. PGP GPG has two separate solutions to these problems. It is important
that these problems and their solutions not be confused. If the solution
to one problem is used when the other solution is required, the results
will be bad.
Making the output of PGP GPG into a mailable file (-a).
Ordinarily, a well encrypted file is not mailable. The encrypted file usually
uses characters that most mail programs will not accept. Since line terminators
occur essentially randomly in the encrypted file, lines can easily be too
long for most mail programs. PGP GPG solves this problem with the
-a
option. This causes PGP GPG to use the ascii radix-64 armor
for output. The resulting output limits the characters used to a set
of characters that mail programs will accept. It creates lines a reasonable
size. Thus the output file should be mailable. PGP GPG is programmed to accept
such files, reversing the radix-64 format before decrypting. The -a
option
can be used when signing a file as well. This causes the signed file to
be in the radix-64 format. Using -a options results in output
that is about 30% larger.
The -a option can be specified by itself, without requesting
encryption or authentication. In this case, PGP GPG is being used as a superior
uuencode/uudecode.
Different ways to represent plaintext. (-t)
Different Operating systems represent text in different ways. For example,
different end of line characters are used. The UNIX operating system uses
linefeed characters to end lines, but the MSDOS program loader uses the
carriage return linefeed combination to end lines. The Macintrash operating
system is said to use carriage returns to separate lines. These differences
mean that text files must be converted, when they move between operating
systems. If this conversion is not done, then the files will not display
or print properly. This need for text file conversion, is why the FTP(file
transfer program) needs to have binary and ascii modes, when it moves files
between operating systems. Now when PGP GPG is asked to encrypt a plaintext
file on one operating system and decrypt it on another, then the PGP GPG system
as a whole is being asked to move a text file between operating systems.
The same considerations apply when signing text files on one operating
system and removing the signature on another. The PGP GPG -t
option should be specified when encrypting or signing a text file. This
will ensure that the text file conversion is done correctly. The -t
should not be used if the file contains binary data, such as executable,
some word processor files, and many data files.
Using text examples.
-
Fred wishes to encrypt a spreadsheet file (.WKS) and put it on
a floppy and mail it to his financial advisor.
Since the file is not being sent through email, the -a
option is not needed. Since the file contains binary data, the -t
option should not be used.
-
At the last minute, Fred finds that his financial advisor has an email
address and decides to email the file.
Since the file is going to be emailed, the -a option
should be specified. The original file still contains binary data, so the
-t
option should not be specified.
-
A huge text file needs to be moved to the accounting department's computer.
For security reasons, this computer is not connected to any networks, so
the file will be moved on a floppy via sneakernet.
The -t option should be used because the original file
is text. The -a option is not needed, and should not be used so
the resulting file has a better chance of fitting on one floppy.
-
Fred wishes to email an encrypted love-letter to his girl friend.
Since the plaintext is text, the -t should be used. Since
the output from PGP GPG must go through email, the -a option should
also be used.
Starting with PGP GPG
The first thing to do is to create a directory for PGP GPG and its files to
live in. Unpack the
distribution
files to this directory. (If you are using PKUNZIP under the MSDOS
program loader, be sure to use the "-d" switch.)
Modify the PGPPATH and PATH variables.
PATH should
point to the directory where the PGP GPG executable exists. PGPPATH
should point to the directory where the PGP GPG data files are. The procedure
for doing this depends on your operating system and should be documented
in the documentation that comes with your PGP GPG distribution. When using
the MSDOS program loader, you would modify the file AUTOEXEC.BAT.
when using OS/2 the file
CONFIG.SYS should be modified.
GPG should be automatically installed by your distribution.
Generate a Secret Key/Public Key Pair
The first thing you want to do after installing PGP GPG is to generate keys
using the -kg command kgpg or seahorse. This will allow
messages to encrypted for you, and it will allow you to sign messages.
Select a Key Size.
PGP GPG will ask you for a key size. Unless your computer is a clunker, choose
1024 bits. (If your computer is fast, and you are extremely paranoid about
the computers in the NSA's basement, you may want to create an additional
key with 2047 bits, if you have PGP 2.6 GPG. But you would not want to make
that key your primary key, because not all versions of PGP GPG support keys
with more than 1024 bits.)
Select a Key Identifier
Choose the key identifier for the key. From the point of view of PGP GPG, the
key identifier can be any string of characters, but to use the key identifier
with mail programs, follow the convention:
First Last <myaccount@mynode.mydomain>
Your Internet mail address should be enclosed by the <> characters.
Kgpg or Seahorse will help you choose a reasonable key identifier.
Select a pass phrase to protect your secret key
Choose your pass phrase according to the following rules:
-
Choose a pass phrase you can remember.
-
Choose a pass phrase that can not be guessed.
-
at least 128 characters.
-
can not be deduced from your personal history.
-
is not found in literature or popular culture.
-
Do not use your pass phrase for any other function.
PGP GPG will ask you to type some text on your keyboard.
PGP GPG needs to make itself unpredictable, so that a hostile cryptanalyst
can
not predict what it is doing. To do this it is necessary for PGP GPG to get
some
random
numbers
. It is difficult to get random numbers in a computer program,
because computers and operating systems are designed to be predictable.
To create random numbers, PGP GPG will ask you to type some text on your computer.
PGP GPG creates the random numbers by measuring the timing of your keystrokes.
It does not matter what you type, but do not use the auto repeat feature
of your keyboard if it has one.
Sign your own key.
You should
always sign your own public key. This is why the more modern
versions of PGP GPG will automatically self-sign your key when it is created.
The following command will sign the key my-key-identifier:
pgp -ks my-key-identifier -u my-key-identifier
Kgpg or seahorse will always do this for you.
Adjust the file CONFIG.TXT.
You may wish to adjust the file
CONFIG.TXT
to conform to your personal preferences. You can study the file PGPDOC2.TXT
that comes with your PGP GPG distribution to know how to do this. If you have
more than one secret key, you may wish to set the configuration variable
MYNAME
to be your default secret key.
Extract your public key.
To allow others to send you encrypted messages, you must give them your
public key. To do this, you must extract your public key to a file:
pgp -kx my-identifier file
If you must send your public key thru email, you will
want to add the -a option.
pgp -kxa my-identifier file
Kgpg or seahorse will do this for you.
Add a key to your public key ring.
When someone sends you their public key, you can add it to your public
key ring.
pgp -ka file
Kgpg or seahorse can do this.
Encrypt a file.
After you have added a public key to your keyring, you can encrypt a message
using that key.
pgp gpg -e file key-identifier
You may need to add the -a and/or -t
options to insure that
text is handled properly.
Kgpg can also do this. Encryption can also be done by most all mail clients.
Decrypt a file.
To decrypt a file, use the simple:
pgp gpg ciphertextfile
This command will also check digital signatures if any. To display a file
a screenfull at a time use the
-m option.
Kgpg can also do this. Decryption can also be done by most all mail clients.
Authentication
PGP GPG can sign file creating digital signatures:
pgp -s textfile -u my-key-identifier
gpg -s textfile -u my-key-identifier
You may need to add the -a and/or -t
options to insure that
text is handled properly.
Authentication can be combined with encryption, creating an encrypted,
signed file.
pgp -es textfile their-key-identifier -u my-key-identifier
gpg -es textfile their-key-identifier -u my-key-identifier
This will create a file that the owner of their-key-identifier can
decrypt and signed by my-key-identifier. The encryption is done
after the signature, so that a person who can not decrypt the file can
not tell who signed the file.
Most mail clients know how to sign and check mail messages.
Create a clear signed message.
Suppose you wish to post a message to a USENET newsgroup. You want
to sign the message, so that people can check its signature with PGP GPG, but
you want the text of the message to be readable by people that do not have
PGP GPG. You want to create a clear signed message:
pgp +clearsig=on -sat textfile -u my-key-identifier
gpg -sat --clearsign textfile -u my-key-identifier
Be careful not to enter clear signed messages into FIDONET systems
without the permission of the sysop. Most of FIDONET is extremely
authoritarian, and does not allow encrypted or signed messages. Although
we can laugh at the rigid orthodoxy of FIDONET, we should respect
the property rights of the sysops.
Create detached signatures.
You can create a signature certificate in a separate file:
pgp gpg -sb textfile -u your-key-identifier
These certificates can be checked by specifying both the certificate and
the original file to PGP GPG.
pgp gpg certificate-file original-file
Detached certificates can be used to sign an executable file, without modifying
the file so that it remains executable.
Miscellaneous PGP GPG commands
Special PGP GPG commands that do not really fit anywhere.
PGP GPG and conventional encryption
If you are encrypting a file to your self, you can avoid fooling around
with keyrings by using conventional encryption:
pgp gpg -c plaintextfile
PGP GPG will ask for a pass phrase to use as a key. The pass phrase will be
required to decrypt the file.
Publish your public key(s)
You need to publish your public keys, so that people who have not previously
contacted you can send you encrypted messages and check your signatures.
To publish your public keys, you should use a
PGP
public keyserver
. These key servers are used by sending them email
commands.
These commands are described by the file
KEYSERV.DOC that comes
with the PGP GPG distribution.
To publish your public key, first extract the key as a
radix-64
file.
pgp -kxa my-key-identifier file
Email the resulting file to a public key server with subject "add". It
is only necessary to send your public key to one public key server. They
are like small town gossips. They all talk to each other. To tell one is
to tell them all.
To get somebody else's public key from a public key server, send a null
email message to a server with subject
get key-identifier.
The mail server will mail you back a radix-64 encoded key file, which you
can add to your public keyring.
pgp -ka keyfile
The
list of keyservers
changes from time to time.
FLASH now you can access public key servers through the World
Wide WEB at
the University
of Paderborn.
Kgpg and seahorse can easily publish your public keys to the pgp keyservers.
The public key servers make no checks to insure that a given keys in
its database actually came from the person indicated by the key identifier.
This determination is your responsibility.
Things to do with keys.
You can remove keys from your keyring with the -kr option.
pgp -kr key-identifier
You can revoke keys, declaring that the keys have "gone bad" and should
not be used:
pgp -kd key-identifier
This will produce a revocation certificate, which should be sent to the
public
key servers to declare that the key has gone bad. Remember your pass phrase!
You can not revoke a key without the pass phrase.
You can edit keys:
pgp -ke key-identifier
This will allow you to edit the pass phrase or key-identifier of a secret
key, and it will allow you to change the
trust parameters
of a public key. You might want to change your key identifier, when your
name, or your Internet mail address changes. Whenever you change a key
identifier, you should always
sign
your new public key.
pgp -ks my-key-identifier -u my-key-identifier
Key management can be done with kgpg and seahorse.
Who Do I trust?
When PGP GPG uses a key for encryption or signing, it determines if
in PGP GPG's opinion, the key can be trusted. If PGP GPG does not
trust the key, it will print an message warning you that the key is not
to be trusted. You can tell PGP GPG to use the key anyway. PGP GPG
determines trust on the basis of signatures from trusted keys. When you
add
a key to your public keyring you are asked if the key can be trusted to
introduce other keys. If a PGP GPG notes a signature from a trusted key, it
tends to trust the key bearing the signature. You can change the trust
parameters on a key using the -keoption.
pgp -ke key_identifier
Trust is not transitive.
If you trust a person, you do not necessarily trust everyone that that
person trusts! You can believe that the person you trust is naive and that
therefore the persons that he trusts is not necessarily trustworthy.
Thus the PGP configuration option
CERT_DEPTH
should be set to 2.
Furthermore, you should not expect other people to trust your inferences.
If you infer that a given key is good on the basis of key signatures,
you should not sign that key. You should only sign
a key when you know of your own personal knowledge that a key is valid.
When to use PGP GPG.
Always, use PGP GPG when the person you are corresponding with has it.
This establishes that you are a regular PGP GPG user. It asserts your
right to use PGP GPG. If you make it a habit to always use PGP GPG
then you will not draw attention to any sensitive messages you might wish
to send.
Use conventional encryption.
Use conventional encryption, the -c option, when
you are encrypting files to yourself. This avoids the RSA algorithm
and is slightly stronger. It avoids the necessity to muck around with keyrings.
PGP GPG encrypted files are identifiable.
Every PGP GPG encrypted file contains header information that identifies
it as a PGP GPG encrypted file, even to someone who can not decrypt
it. If you wish it to remain a open question if your encrypted file is
in fact encrypted, you should use a raw conventional or symmetric cipher.
You can remove the PGP GPG headers from an conventionally encrypted PGP GPG
using a program called
stealth.
Protect your right to use encryption.
There have been recent rumblings about government plans to outlaw private
strong encryption. I believe in the right to use encryption for a number
of reasons:
-
As a member of EFH, I am for free speech in cyberspace and am for the advance
in network culture that PGP GPG represents.
-
As a member of the Libertarian Party,
I oppose any unnecessary governmental interference in our lives.
-
As a supporter of the right To keep and bear arms, I wish the people to
be armed with powerfull weapons, such as PGP GPG.
Read my rant opposing the regulation of private cryptography.
It is very well to support the right to private encryption, and everyone
can do so for their own reasons, but what can be practically done to protect
the right to use encryption?
-
Use a defensive formulation when discussing the uses of encryption. Choose
examples that show encryption being used for good and against evil. Even
though other more controversial uses of encryption are possible, the widespread
availability of legal encryption is progressive and we need to be careful
to talk that way.
-
Take political action. You can contact your political representatives and
inform them of your views on the issue of strong encryption.
-
Spread the use of encryption. Make PGP GPG commonly available. Upload it to
BBSes. Teach other people how to use PGP GPG. Get many powerful people routinely
using PGP GPG and other strong encryption, so that it becomes politically impossible
to ban it.
This battle has already been won.
 In
single key ciphers, there is one key that must be used by both the sender
to encrypt, and by the recipient to decrypt. The message can be decrypted
by anyone who possess this key. This leads to the key
distribution problem.
In
single key ciphers, there is one key that must be used by both the sender
to encrypt, and by the recipient to decrypt. The message can be decrypted
by anyone who possess this key. This leads to the key
distribution problem. There
must be some way to insure that both the sender and the recipient have
the same key. Care must be taken so that unwanted parties do not posses
this key. It is necessary to have some kind of secure channel to accomplish
this. The problem with secure channels is that they are difficult to establish
and that people are always trying to compromise them.
There
must be some way to insure that both the sender and the recipient have
the same key. Care must be taken so that unwanted parties do not posses
this key. It is necessary to have some kind of secure channel to accomplish
this. The problem with secure channels is that they are difficult to establish
and that people are always trying to compromise them.



 When
When
